WannaCry Ransomware
Attack Name:
WannaCrypt, WannaCry, WannaCryptor, or Wcry virus (a type of ransomware).
Release Date:
May 12, 2017
Targeted Systems:
Exploits vulnerability MS17-010 in Microsoft's implementation of the Server Message Block (SMB) protocol.
Infection process:
Ransomware is a program that gets into your computer, either by clicking or downloading malicious files.
The initial infection might have been either via a worm, spreading by itself within a network or contained within an
attachment to an email that masquerades as something innocent.
Once the attachment is opened, it encrypts the hard drive, making it impossible to access or retrieve anything stored on there.
Virus impact:
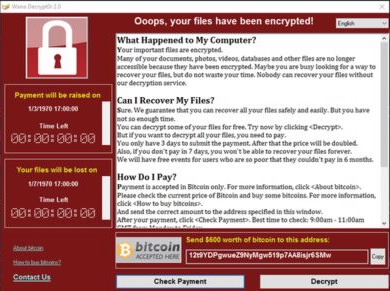
The WannaCry ransomware attack is continuing to spread across the world, impacting over 10,000 organizations and 200,000 individuals in over 150 countries.
Virus is seizing control of affected computers and encrypt all computer data until the victims pay a ransom of 300$ in bitcoins.
Steps to prevent and protect against this threat
-
Microsoft customers must install the security update MS17-010 and do so as soon as possible.
from here
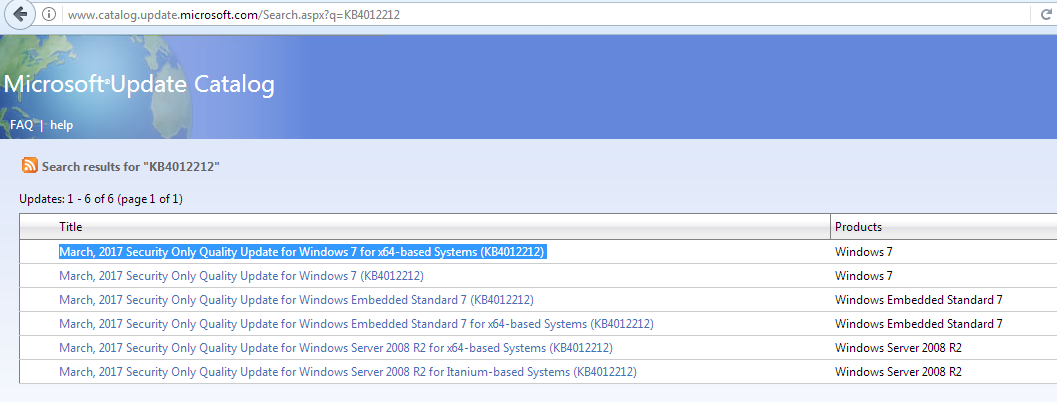
Example: for Microsoft ًindows 7 (64 bit) users, you may go to:
click here
Then download and install the first file
“March, 2017 Security Only Quality Update for Windows 7 for x64-based Systems (KB4012212)”
-
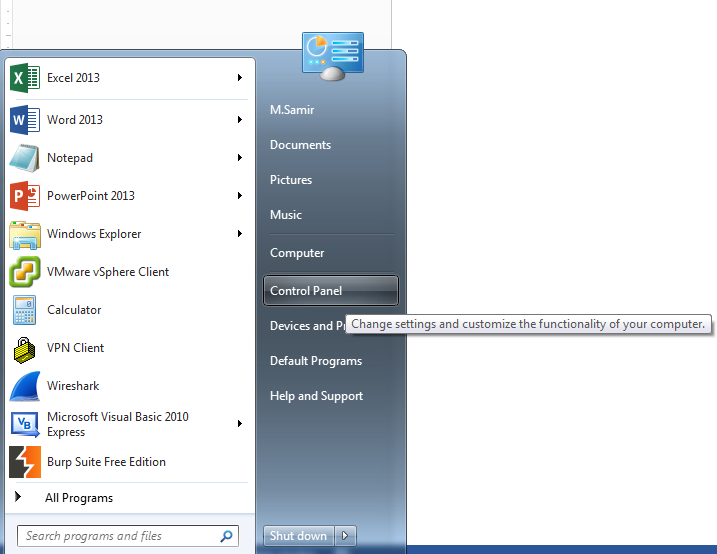
To those how don’t use sharing services:
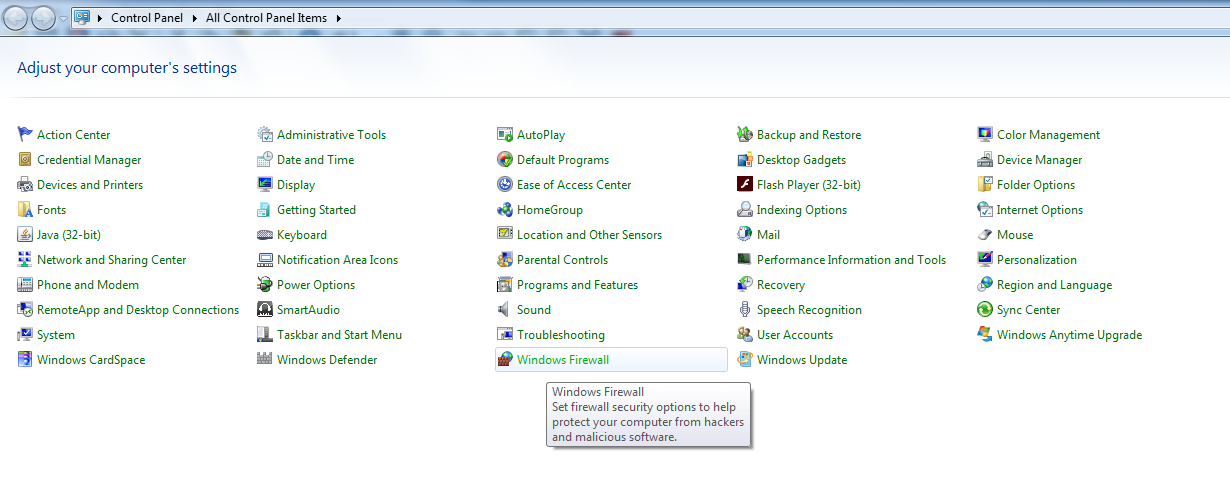
Edit your firewall settings to block incoming SMB traffic on port 445.
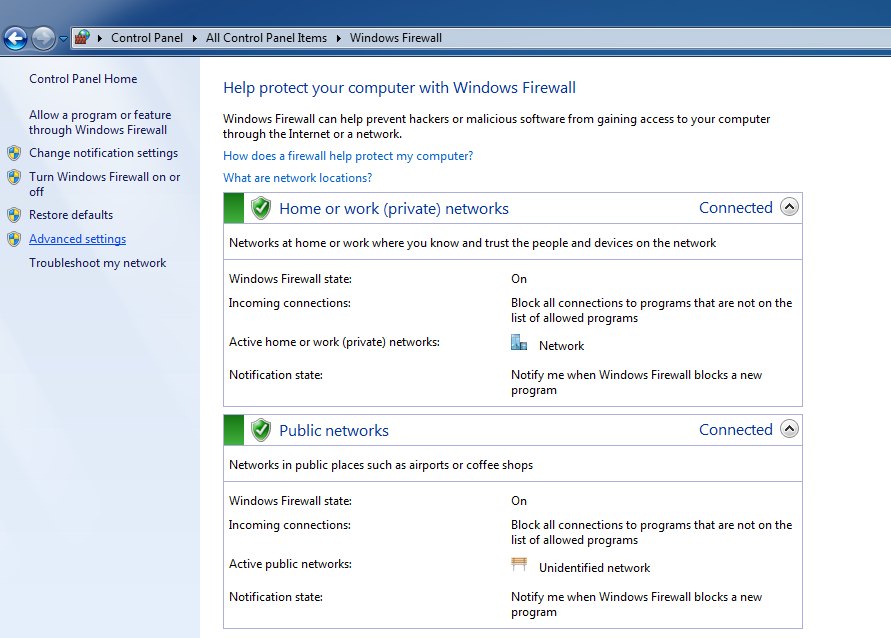
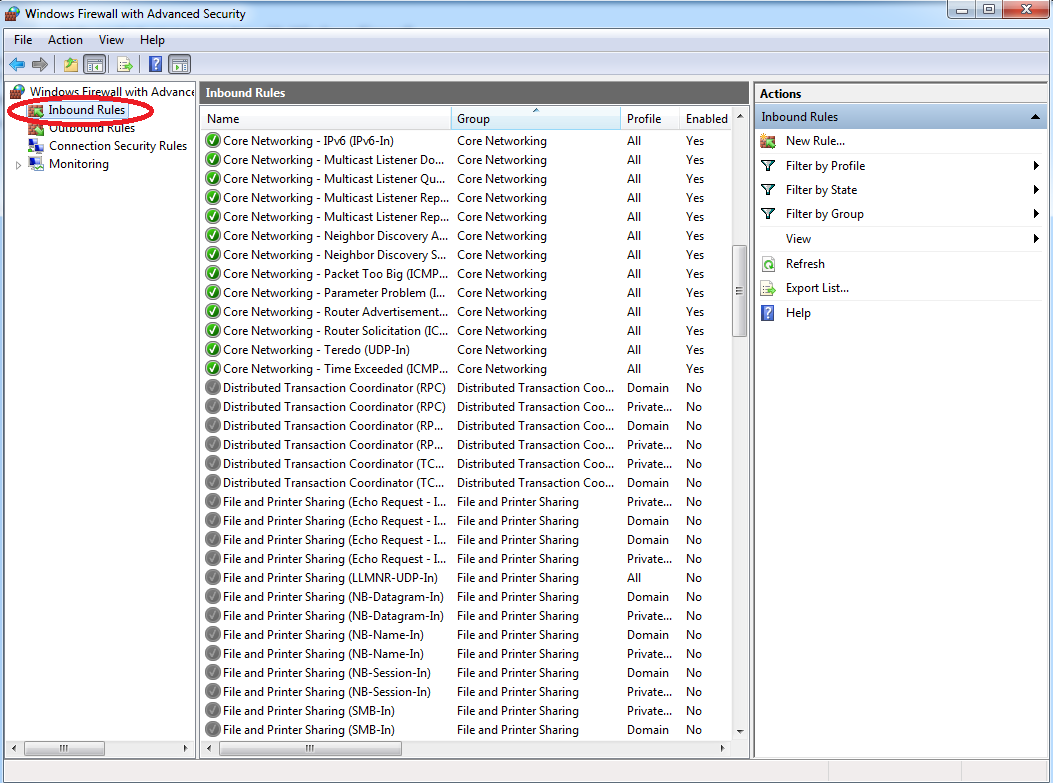
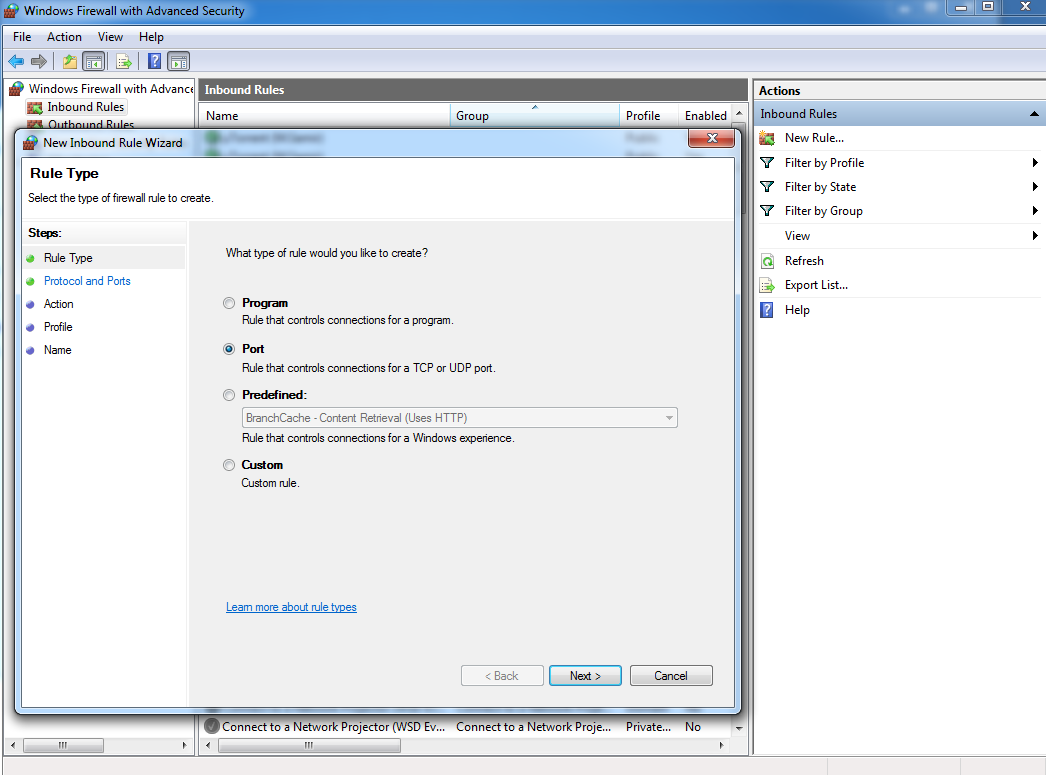
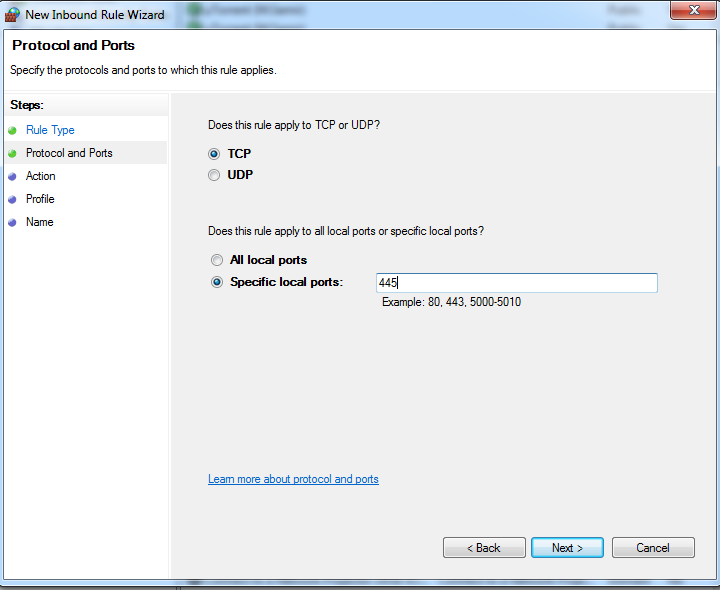
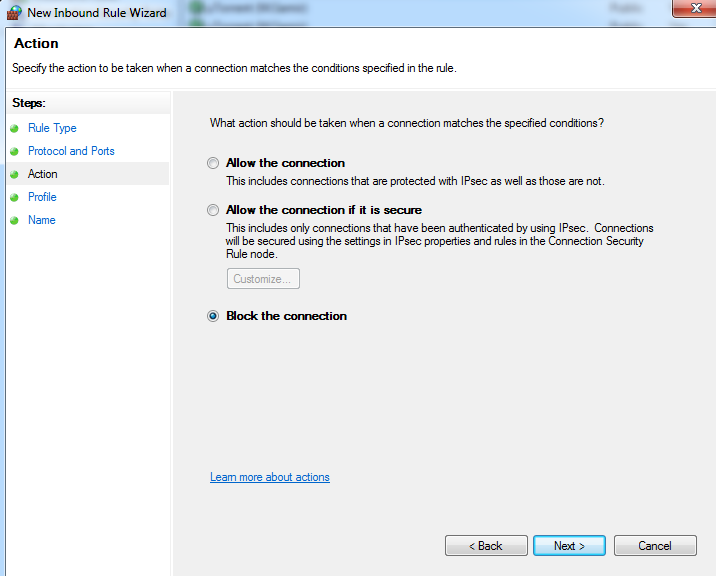
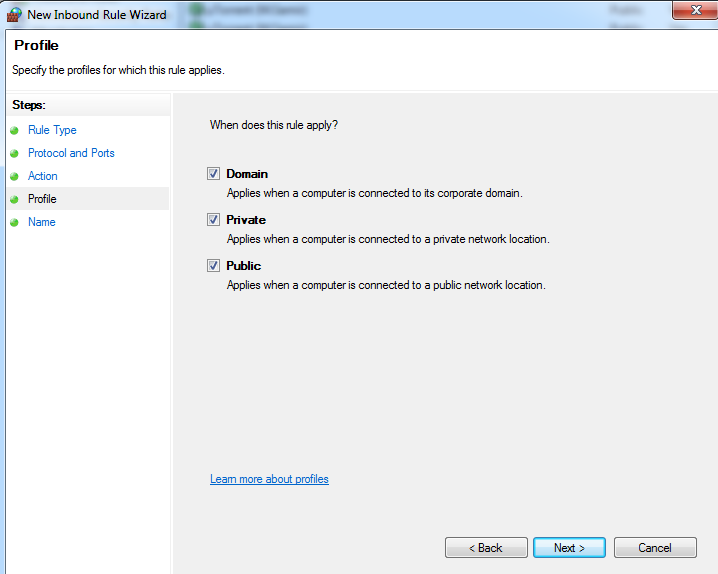
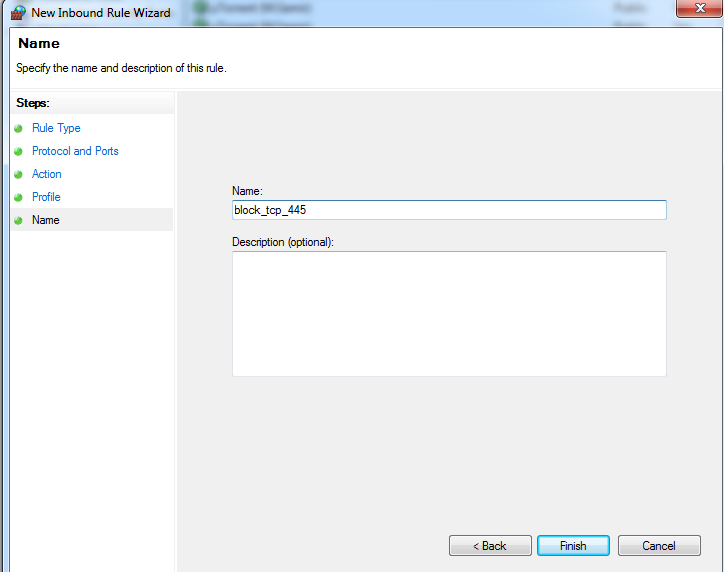
-
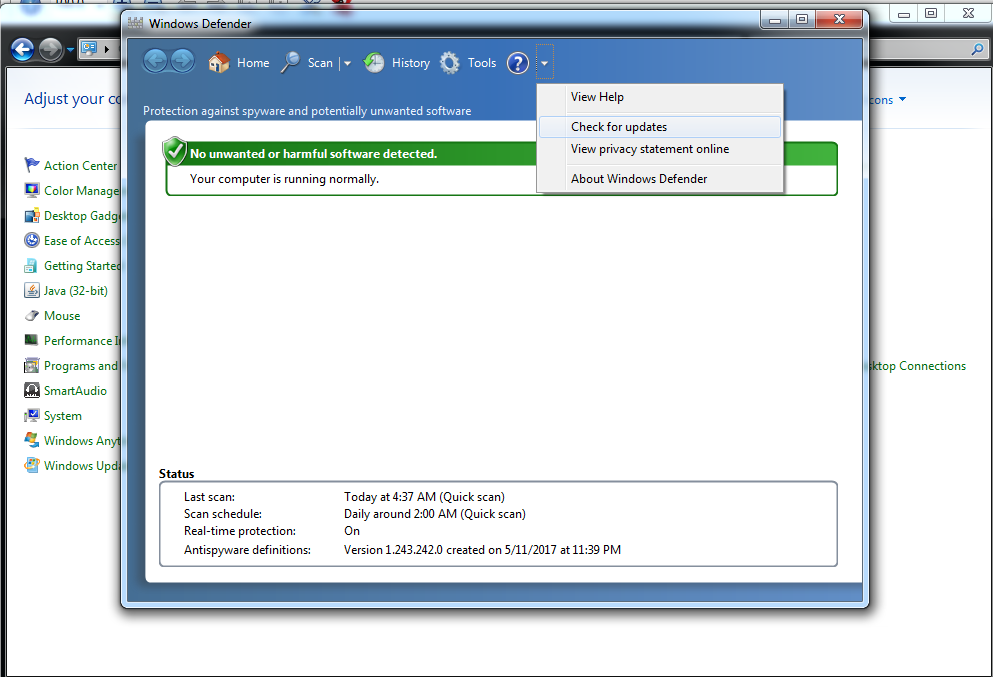
Enable Windows Defender Antivirus to detect this ransomware.
Windows Defender Antivirus uses cloud-based protection, helping to protect you from the latest threats.
-
Make sure to install and update your Antivirus client to the latest version.
-
If you are not using any sharing services,
you may need to disable SMBv1, SMBv2, SMBv3 with the steps documented at Microsoft Knowledge Base Article 2696547
click here
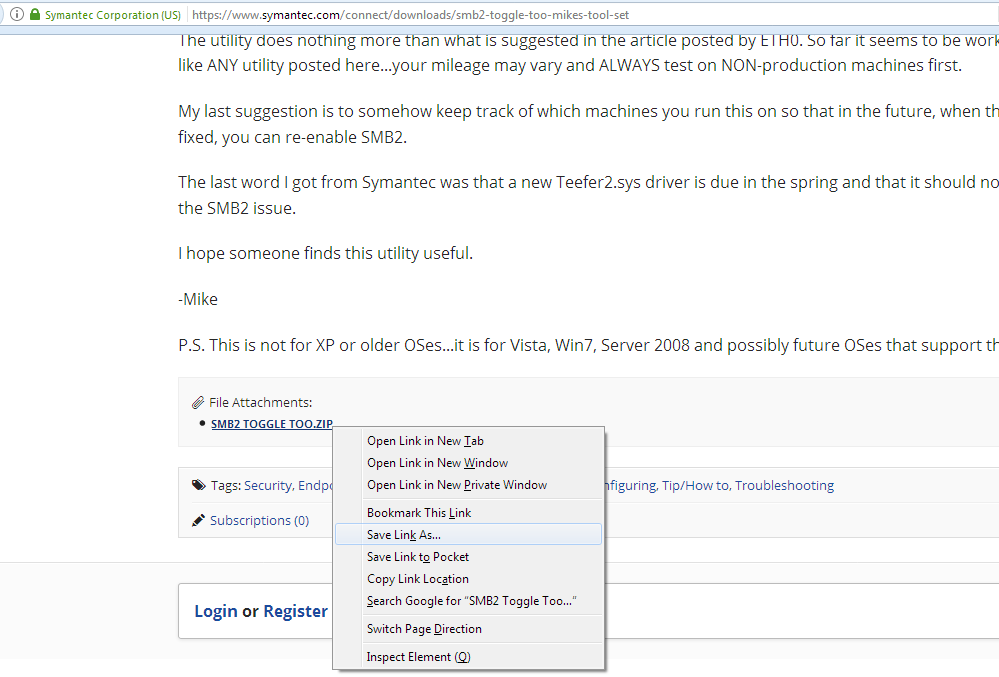
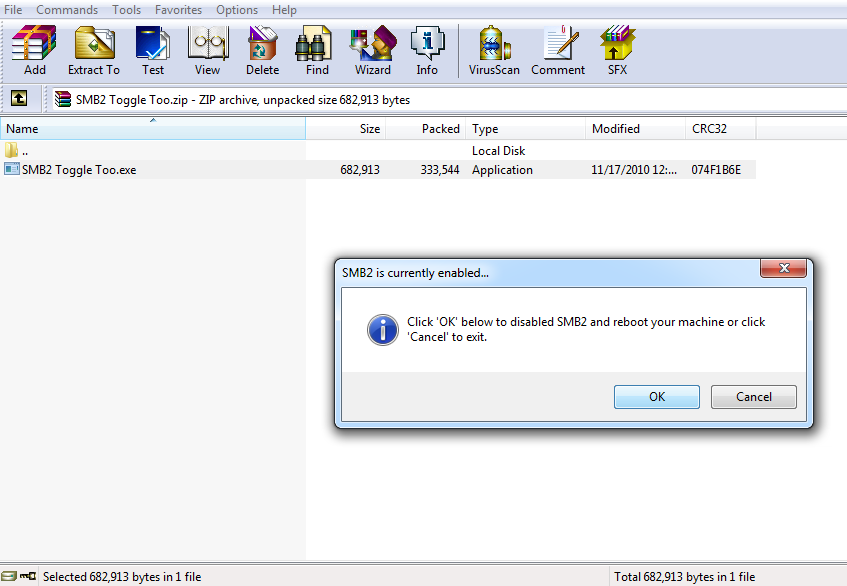
Or, you can simply download and run Symantec removal tool “SMB2 Toggle Too.exe” from
here
General preventative measures
-
Update your operating system regularly
- Use antivirus software and update it regularly.
-
Back up data regularly. Verify the integrity of those backups, encrypt them, and test the restoration process to ensure it is working properly.
-
Scan all incoming and outgoing emails to detect threats and filter executable files from reaching end users.
-
Schedule your anti-virus and anti-malware programs to automatically conduct regular scans.
- Do not open suspicious emails from untrusted sources.